Like many other technologists, I am also fascinated by the wide spectrum of possibilities made with machines. Social Media is one of the prime examples of a “thing” that managed to become a mainstream method of building online relationships. In some regions, it’s even perceived as the Internet itself. Yet, the tremendous privacy abuse, political manipulation, and mental toll can’t be a “necessary evil” characteristic. It’s time to Build Better Systems.
Facebook as a symbol of Social Media
It’s easy to point a finger at Facebook because they are the biggest behemoth. They are a huge corporation, that controls few networks and represents the growth and the decay of what is defined as social media. Yet, the critique applies to every entity that chooses unethical business practices.
Moreover, because they can effectively influence public opinion with their platform, Facebook plays a constant PR “apology game”. With every new controversy, they choose to flatten, but not solve the issues that negatively impact their users and the real world.
In other words, Facebook is an example that should be recorded, analyzed and saved for posterity. If they’ve managed to find a “magical formula” for building and monetizing user interactions, it means that any other company can re-create and follow the same dark pattern.
What is the core of social relationships?
Humans evolved as social creatures. For most of our history staying with the tribe/community/nation meant higher chances of survival. Caves, ancient forums, or a room in a cultural center – those were the physical places where we have been growing our interpersonal relationships.
With the rise of the Internet and mobile technology, more and more people started to replace physical places with virtual ones. And then came Facebook. Inspired by the ingenuity of Google, they build better systems than web forums, phone calls, and text messages.
Facebook re-created “free” rooms, public squares, telephone lines, and post offices on their own platform. The only thing a user needs to do is to accept their terms and privacy policy. But let’s look at the striking differences between the former social places and Facebook.

Traditional social places vs social media
| Characteristic | A room in a cultural centre | Facebook platform |
| Who owns the space? | Local city council | Privately managed corporation |
| Who creates rules that affect people? | People participating in the gathering | Facebook creators |
| How to oppose and discuss alternative rules? | Talk with the city council and/or gathering organizers | No feasible path for dialog with Facebook creators |
| What is the legal binding? | Constitution and regional laws | International and national regulations – IF they are created and enforced (i.e. GDPR, CCPA) |
| Who can watch and listen to interactions between people? | Only the participants of the gathering | Facebook employees |
| Who can record and analyze all interactions between people? | Participants themselves – ONLY IF they want to | Facebook servers and algorithms |
| Is advertising based on people’s interests allowed? | Participants have full control over any commercial activities during the gathering | It’s a core of the Facebook business model and users cannot use the platform without being tracked |
| Are my personal details stored, recorded, and analyzed, even if I don’t participate? | No | Yes. Facebook creates shadow profiles for everyone in their extended reach and merges them once you decide to join the platform |
| Who has (intimate) insights about my relationships with others? | Only participants of the gathering and trusted contacts IF you decide to share some information with them | |
| Who can get access to sensitive information about a person? | Nobody | Anybody who can afford to pay for targeted advertising (the price of a used car) and then cross-reference it with additional public/commercial records (i.e. Cambridge Analytica controversy) |
In other words, physical social spaces like a room in a cultural center is a safe space, where you can interact with other folks. The joy you feel while taking dance classes and the amount of time you spend talking with this one special person stays within the group. It’s yours.
The virtual social space created by Facebook feels similar because you focus on people, rather than on technology. Yet Facebook is the one that measures and monetizes the exact time you spend interacting with your romantic interest. And your friends, co-workers, family, and everyone else in the proximity of Facebook’s tech.
The core of social relationships is enclosed in little moments. Moments when we watch the youngest family members speak their first words or when we hike with close friends during a sunny day. This is a priceless invisible web that we have been building from the dawn of humanity. It shouldn’t be a privatized marketplace owned by Facebook or anyone else.
Who made the Social Dilemma doc?
Complex topics require solid storytelling structure to communicate the message. Prior to Social Dilemma Jeff Orlowski directed Chasing Ice and Chasing Coral – documentaries about intricacies of climate change. Both of them show how whole ecosystem landscapes are changed by human activities. Jeff knows how to present the scale of the problem and then explains the crucial elements that build the big picture.
Social Media’s underlying business model is no less intertwined with our lives than climate change. And Tristan Harris, co-founder of Centre for Humane Technology, is the right narrator to tell the story of inhumane big tech practices. I’m a regular listener of Your Undivided Attention, the podcast produced by this nonprofit organization, where Tristan and Aza Raskin (the other co-founder) are talking with key people striving for humane tech.
In 2010 The Social Network movie was a colorful Hollywood tale about a computer genius. We, the people in and outside the US were mesmerized by the very first Internet phenomenon that truly “connected us all”. In 2019 the Great Hack crashed this dreamy perception by revealing the scope of power abuse done with uncontrolled data hoarding.
You can think of Social Dilemma as the third part of the infamous trilogy. The rise, fall, and fall even lower of a platform that influences our everyday life – even if you choose to delete your account. Each movie presents foundational concepts, necessary to understand the systems in control.
Why great systems are important?
For me, it’s natural to apply a computer operating system analogy to other aspects of life. As a nerd, my work and interests are deeply rooted in wide-ranging technology. Regardless of your digital literacy, we all live in the information age, therefore it’s practical to apply this “system thinking“.
Water irrigation in ancient Mesopotamia is an example system where people stopped relying on the environment. Agricultural control over food allowed a more stationary way of life and eventually lead to building cities and civilizations. This is, of course, intertwined with a concentration of power and a long period of autocracy.
The food production system established a political power system
We are fortunate to live at a time when most countries value and strive for democracy. In a very simplified perspective this political system:
- distributes the power to many more people,
- has built-in time constraints, that forces changes of leaders,
- auto-corrects itself with institutions that try to keep checks and balances across the board.
Better systems build civilizations
Civic societies thrive on well-designed systems. Various regulations, protections, freedoms, and international unions among others allow for self-governance and growth. In other words, the concentrated political power (autocracy) was replaced by a better system of distributed political power (democracy).
The well-being of growing populations has been always linked to water treatment systems. In the middle ages, diseases spread faster and were more deadly, because the same river functioned as a source of water and sewage. Today most places build better systems of acquiring water from a spring and filtering contaminated water that flows in separated pipes.
A similar shift happened to capitalistic abuses. Slavery and child labor have been banned and job regulations protect employees. A primitive system of maximizing capitalists’ profit over human lives has been replaced by a better system of compensations, sick leave, holidays among others.
A different perspective – compare social media to other industries
It’s crucial to understand the complex network of incentives that drive the growth of any industry. The relentless rate of social media influence over everyday life can be viewed from the perspective of other not less influential systems.
Oil
The petroleum industry is on one hand the major source of life-saving pharmaceutics and convenient means of global transportation. On the other hand, it’s destroying environments and polluting human habitats more than anything else in the past.
Sugar
Sugar is the first taste we sense as babies (lactose in milk) and we tend to associate comfort meals with anything sweet. The processed food industry capitalizes on it by maximizing sugar amount in any product (bliss point) and keeping customers hooked. The more sugar you eat, the more you want it.
Television
We all have favorite tv shows and cozy memories associated with sitting and watching movies together. It resembles tribal traditions of gathering around a bone fire and sharing oral stories. Yet television is also a masterpiece example of building echo chambers, political propaganda, and a distorted view of reality.
The current construct of the social media business model seems like all of these industries before civic societies develop effective methods of regulation. For reference, here are some capitalistic abuses that have been caught and corrected by affected communities:
- Car manufacturers tempering with diesel exhaust certifications lead to a planned ban on selling internal combustible engines in many territories.
- To countermeasure, rising child obesity schools are removing fast foods, soft drinks, and sweet snacks from cafeterias.
- Television programming used to be completely in control of the channel owners, but today many countries have rules to limit indecent content during the day, secure equally shared playtime for political ads, and maintain separation of public media from political misuse.
The current state of social media is like driving a car without speed limits and seatbelts in a neighborhood with small children and elderly people. Everyone is affected because even if you don’t drive the car (don’t use social media), most people around you do it. Car accidents (social media misuse) have a strong impact on the wellbeing of the whole community.
What to do after watching the Social Dilemma?
Societies around the world faced seemingly impossible challenges before. Our endurance keeps us going forward and I honestly believe that we’ll find solutions to issues showed in the Social Dilemma. Global diverse perspective and my long-term digital nomading in various countries are what keeps me optimistic. I don’t just hear stories of communities that manage to stand up to the “giants”. I talk to people and live in places that directly feel the effects of strong policies.
How people solved this issue elsewhere or in the past?
If you already watched the Social Dilemma, you understand that there’s a complex net of problems, created both directly and indirectly by big tech, advertising, and relentless capitalism. The following examples are addressing some of them and it’s crucial to recognize that solutions can exist on the international, regional, and individual level.
European GDPR is a prime example of an international level directive that affects all companies operating on the Internet. In short, GDPR requires direct consent from each user for every single type of data management – marketing, reselling, analytics, etc. Its significance is visible by imposed fines and other regions that are implementing similar GDPR-like policies:
Taiwan is a unique region, that in my opinion, is currently forming world-class standards for combating disinformation and encouraging citizen participation. Their “Humor vs Rumor” campaign keeps track of spiking topics across social media in Taiwan, then determines if a piece of information is manipulative (Rumor), and creates a funny counter-message (Humor) that spreads faster than a rumor. On the other hand, the g0v (pronounced gov-zero) initiative allows anyone to create policy/project similarly to a software app. If the new idea introduces crucial improvement and gets enough upvotes, it’ll be implemented by the government as a new official policy.

Then there’s this personal level dependant on our unique circumstances. Meeting friends and romantic interests have historically been tied to physical proximity and local cultural code. Social media enhanced ways to meet new people. But at the same time, all interactions (likes, messages, calls, check-ins, meetings) have become a valuable hyper-localized business resource. That’s why it’s so important to remember the timeless ways of social connections. You can still meet new folks by:
- picking up a new hobby and meeting fellow hobbyists,
- asking a good friend in arranging a date with someone else,
- listening to stories of how your family members found their partners or best friends and then trying new ways on your own.
What helps you grow?
This question requires self-awareness. If you have trouble finding straight answers I do recommend testing and observing the things that truly contribute to your growth. In my case that would be:
- long-term traveling,
- creating (writing, web dev, designing),
- listening to audiobooks/podcasts,
- walking,
- regular exercises,
- thoughtful conversations.
I became aware of all of these important activities due to mindful meditation. It’s a powerful tool that requires time, effort, and practice. Without it, I wouldn’t be the person I am to today. Moreover, I wouldn’t strive to fulfill my ambitious dreams. The beauty of mindfulness is in fact, that I learn to appreciate the whole journey.
What is the minimal digital setup?
How do you know when it’s too cold for you? Or when to stop drinking water? Evolution equipped us with powerful receptors that can instantly send the right signal to the brain. Then the conscious reaction is to wear more clothes or put down the glass. In short, we already know, when we have enough.
The same is possible to achieve with more sophisticated things but requires more trial and error. When I started working in tourism in 2005 I was sure that I need to carry the biggest possible travel bag plus a backpack full of electronics. Because “I never know what will be needed”. After years of testing, I constructed a customized method to determine the most important items.
Either it is a travel gear, devices, or apps that I use – I apply the same mindful questions for every single object that is on a journey with me:
- How many times a week do I use it?
- Is there a lighter/better alternative to what I use?
- How does this thing retain value over time?
Check my current minimal digital setup.
How my approach to social media changed?
These questions can be also applied to “free” apps/services, even Social Media. For me, Instagram was definitely the most important, when I started using it in 2011. While I still enjoy posting pictures from my adventures, I schedule daily uploads via Buffer and open the mobile app at most three, four times a week. If you want to present your travel pictures – creating a blog is a much better and long-term alternative to IG. Also, if you want to allow others to use freely your creative pieces, then Unsplash is an amazing photo community for that.
Initially, the Instagram value was in a photo-centric app that gathered artistically oriented folks. Over time it became television, where ads and “reality TV” influencers are jumping to new media formats (video, vertical, live, etc.) to fight for users’ attention. For me, the value is still in niche creators and their original art pieces shared organically.
Some of my favorite creators:

The purpose of asking these questions
Every one of us is on a spectrum of susceptibility. Even if you feel that you’re resistant, there’s always a signal that can trigger you. Social media represents the most cutting-edge susceptibility solutions developed by social-behavioral scientists, data analytics, and engineers. Yet the business principle is similar to phenomenons in the past. TV, colorful magazines, and yellow journalism all build their business on sensationalism and exaggerations.
That’s why reasoning and critical thinking have been and still are essential skills. One of the ways to improve them is by asking the right questions. Sometimes a set of problems seems to be too complex (i.e. climate change), but if we start from the lens of a few well-crafted queries – it’s easier to grasp the big picture.
To re-iterate:
- How people solved this issue elsewhere or in the past?
- What helps you grow?
- What is the minimal digital setup?
I do believe that the above questions are useful to you, as much as they are for me. Please spend as much time as you need to find satisfying answers. Additionally, there are some books that may be a helpful guide for your unique situation.
We have paleolithic emotions, medieval institutions, and god-like technology
Edward Osborne Wilson – entomologist and biologist
What sources can help in finding the right answers?
Digital Minimalism – stay in control of your devices and apps by applying a practical set of rules. This book can help you understand when, for how long, and for what specific purpose you should use every device.
Tao of Seneca – the timelessness of stoic philosophy is a remarkable feat started by ancient Greek but remained valid and cultivated throughout the ages. Imagination is a powerful tool that stoics use frequently to run thought experiments necessary to reach calmness. Regardless of how chaotic is the world around you, stoic principles can be your mental immune system that works relentlessly.
Search Inside Yourself – mindfulness described as a tool. The whole book is written from the perspective of a humorous engineer spreading great vibes – first internally at Google and now in a form of a structured program of mindful meditation. It’s a good place to start your journey with mindfulness.
Centre for Humane Technology is actively working with many institutions to teach good online practices and to build better systems. They understand the importance of working on individual, regional, and international levels. Therefore regardless if you just want to be a more conscious Internet user or you represent an influential organization, I do recommend reading their site:
Abusive practices of capitalistic digital systems
As a global society, we are still in the Internet phase of the free-for-all gold rush. The economic freedoms for a vast amount of people outweigh the negative phenomenons. That’s one of the reasons why governments are so reluctant to impose heavy regulations. They may break the “magical wealth machine”. Therefore, as history often reminds us, when the leaders fail, people are not afraid to oppose. For example by civil disobedience.
Please keep in mind that civil disobedience is a spectrum and you should consciously perform only these actions that you are comfortable with. Anything from setting a time limit for social media use, engaging in the discourse, to participating in peaceful protests can be part of your civil disobedience. Your contribution is an important block in building the resistance against corporate-driven unregulated capitalism on which big tech sits.
To strengthen the message, I’d like to iterate once more. Civil disobedience actions have to go inline with building better systems. Systems that are:
- more just,
- unlock equal opportunities,
- representing the diverse culture of all participants.
How do we know that the current state of the data marketplace is abusive?
In 2019 three highly relevant books summarized decades of technological and political advancements that resulted in the current situation. While watching The Great Hack and The Social Dilemma made you aware of the underlying problems, the following titles will build your deep understanding.

Permanent Record – know your digital fingerprint
Edward Snowden is known for disclosing the global surveillance practices of American intelligence agencies. In 2013 his whistleblower actions were condemned by the US government, but in September 2020 the federal court ruled that the exposed surveillance program was illegal. This is a valid factor proving the importance of Snowden’s work. His Permanent Record is a detailed memoir that starts the story with Ed’s patriotic upbringing and passion for technology.
In later chapters, you’ll learn about the massive growth of surveillance technology after 9/11. Its scale is almost unimaginable and in many instances sickening – operatives listening to private conversations of Indonesian family or exchanging private nude pictures of unsuspecting women. While nobody can predict how these mass surveillance systems will evolve, each one of us is in control of our digital fingerprints.
Every uploaded photo, published comment, or liked post is feeding the “machine” capable of computing and learning about your personality. That is true as long as you willingly leave identifiable traces, so any network or service provider can pick them up. Snowden in the book and at Freedom of the Press Foundation is focusing on encryption but also practices for maintaining privacy in the digital age.
Targeted – know how the digital fingerprint is weaponized to destroy democracy
Ubiquitous Internet access allowed many people to find like-minded friends, regardless of how niche is their hobby. Social Media is making money by providing easy-to-use community-building tools and selling user data to advertisers. The by-product of this ever-enhancing machine is hyper-localized political ads – especially towards the most vulnerable individuals.
While political propaganda is as old as political systems, the precision, custom-made messages crafted for specific groups and instant digital delivery is a novel phenomenon. Cambridge Analytica is the most known company responsible for dozens of political manipulation campaigns and Brittany Kaiser is their former employee.
Her book “Targeted: The Cambridge Analytica Whistleblower’s Inside Story of How Big Data, Trump, and Facebook Broke Democracy and How It Can Happen Again” is focusing on:
- SCL Group (Cambridge Analytica’s parent company) involvement in psychological warfare
- Data mining and data analysis (including cross-reference) for detailed user personalization
- Deliberate unethical executives’ decisions for the sake of earning money from the highest bidder (i.e. 2016 Trump campaign, Leave.EU Brexit campaign)
Political polarization via Social Media in the USA and the UK is also happening in other countries and Targeted is an important account of what went wrong. Moreover, Kaiser is also running the Own Your Data Foundation, which advocates for establishing proper data policies on the international/regional level. For individuals, the foundation teaches digital literacy – awareness and individual practices that can help to stop the abusive tech business patterns.
The Age of Surveillance Capitalism – Who knows (your digital fingerprint)? Who decides? Who decides who decides?
These are three fundamental questions that Shoshana Zuboff is asking in her book. After about two decades of conducting researches and interviews, she combined an extensive report on the new kind of capitalistic system. It’s one where every single action of every person is being recorded and then turned in to an ever-improving subtle influence machine.
Zuboff points to behavioral surplus data that Google gained at the moment they started to store users’ search queries. It opened up the possibility of detailed profiling interests of every person. Facebook followed their example and added existing social ties to determine character traits and even to create shadow profiles for people not yet in the network. Lucrative automated advertising services were introduced by both of these companies to monetize stored behavioral surplus.
Please mind that Google and Facebook are the most visible examples but the core of the problem lays in the “free-for-all” form of capitalism. We are all in this inflection point, where data is more valuable than oil and companies want to make a profit out of it. Yet, the same data can be weaponized against minorities, political opponents and to fuel outrage. Analogically as societies were drastically changed by industrial capitalism, now we face the real-world effects of surveillance capitalism.
“Are we all going to be working for a smart machine, or will we have smart people around the machine?”Question asked in 1981 by a young paper mill manager – The Age of Surveillance Capitalism
Three vital questions
In the past, if you wanted to share the good news of your firstborn child you were telling it directly to your closed circle (Who knows?). You chose who is trustworthy to know about it, and maybe they pass it to friends of friends (Who decides?). In surveillance capitalism, the first “friend” that knows is the private company that stores your baby photos in the cloud. They can decide to automatically scan the photo, see you are a new parent, and sell this information to diaper manufacturers to display a customized ad. Without any additional oversight (Who decided who decides?), the capitalistic transaction has happened before you had a chance to talk to your human friends.
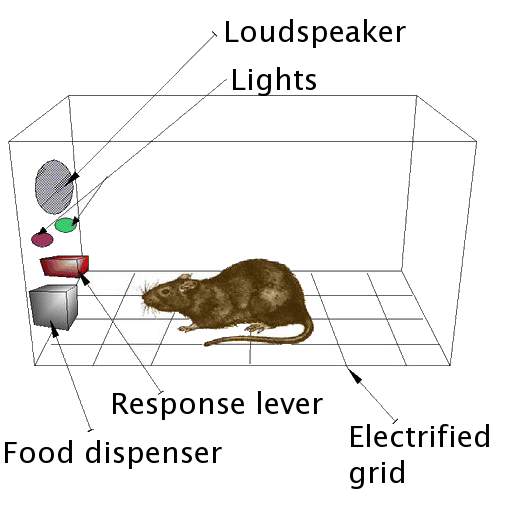
All of these details are explained by Zuboff with scientific rigor and with dozens of historical cases. She highly critiques American psychologist, B. F. Skinner who considered free will as an illusion and suggested reinforcing human actions, the same way animals are reinforced in the operant conditioning chamber. His radical behaviorism is principal for surveillance capitalism. That’s why it’s crucial to counterweight this simplistic profit-driven practice with nuanced democratic policies for the well-being of us all.
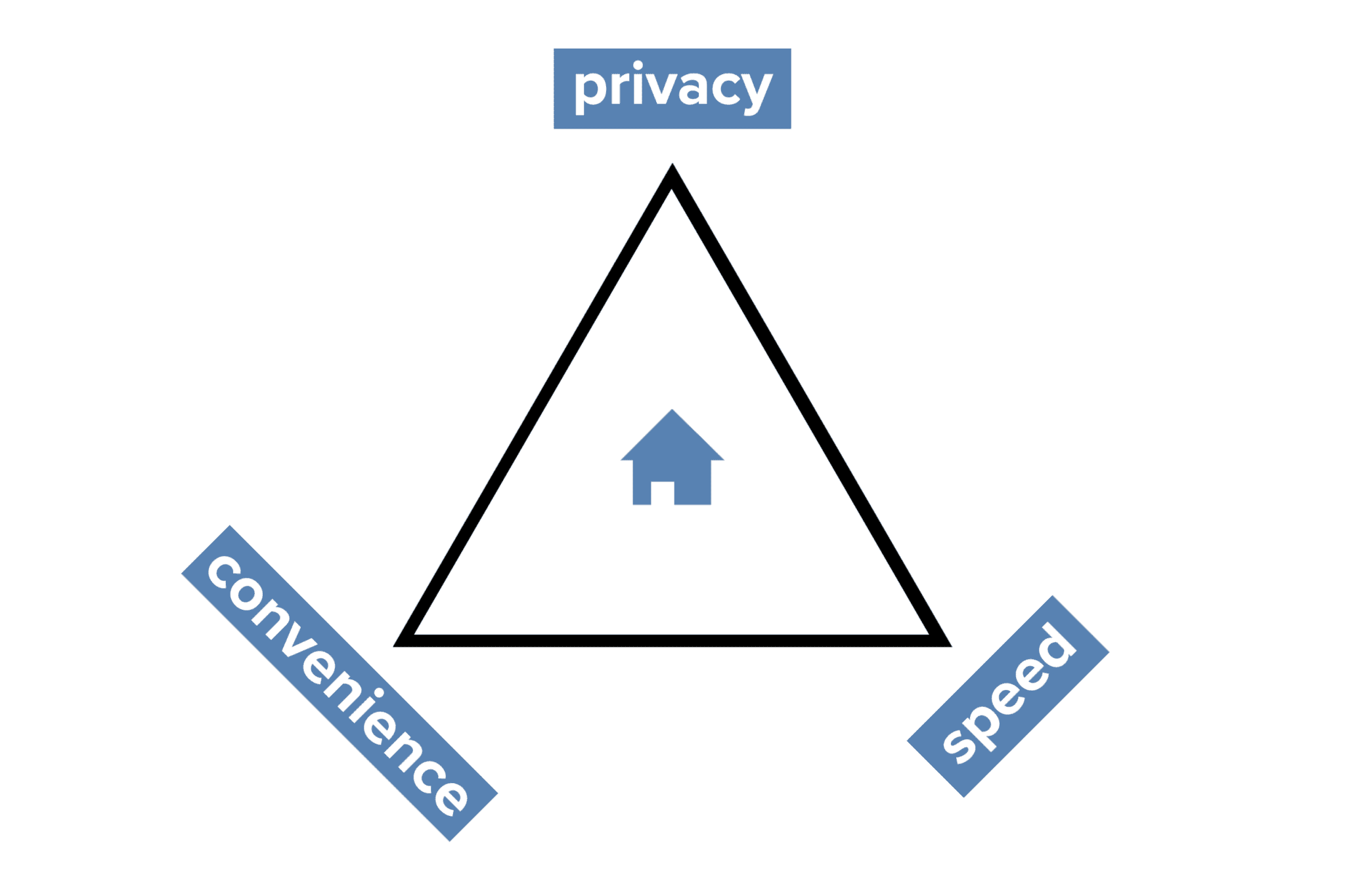
Convenience, privacy, speed – pick two
From the very beginning of its existence, the Internet is mimicking the real world. Sending letters is replaced by e-mail, talking to a friend on a bench is done via chat apps, and cheering for the favorite team at the stadium is now happening in e-sports. Therefore, if social-bonding is now happening online, we need to consciously recognize and protect these common spaces. A good analogy is a corporate-controlled city with gatekeepers (Facebook) and an open-for-all public park (the whole of the Internet). The key question is – where do you build your digital house?
Facebook or any other profit-driven company always wants to lure the masses in. With flashy neon, loud sounds, and perceived convenience – “we just need your name, then everything is for free”. It also comes with perceived speed – “if all my friends are there I can quickly reach them”. The undeniable heavy price in this exchange is privacy. If one company can see through your digital house, they decide how to sell details about your political views, sexual orientation, and favorite cereal brand.
Digital privacy = real-world privacy
John Gruber from the Daring Fireball website published an article “Online privacy should be modeled after real-world privacy“. While the piece is written in regard to Apple’s postponed enhanced privacy features in iOS 14, it does have a timeless message. Our digital houses need to have:
- sun shades – methods to block visibility for companies/advertisers/other people,
- door locks – proven security measures to protect against cyberattacks,
- smoke alarms – clear signal in case of a privacy breach,
- blueprint schematics – the underlying structure is transparent and easy to check by a specialist.
This interpretation gives you also the realization of how fast things should work. Of course, it would be faster to run in and out of a house that has no door locks. Or even better – no doors at all. If it takes too much time to open and close shades, why bother having them? At the point of total free flow in your house, you’d probably not even hear the smoke alarm, because of the constant noise. Blueprint doesn’t exist because the “house” is more like a cargo container – shaped, moved, and adjusted by the outsiders. Not by the inhabitants.
Therefore, convenience, privacy, and speed on the Internet are like opposing vertices of a triangle. Your digital house can be placed on this spectrum, but mind that these values are subjective and evolve over time. Security standards change accordingly to cyber threats and what is easy to use today, can be slow and inefficient tomorrow. Still, the point is to be mindful of your choices.
Practical digital solutions to minimize data hoarding and data exploitation
I believe you already see the pattern, that digital literacy is an essential skill in the current age. It’s the ability to read and comprehend all kinds of digital messages. Aforementioned Audrey Tang, the digital minister of Taiwan, goes a step further and develops digital competency within her country. I concur. For the wellbeing of the global community, we need a deep understanding of the digital infrastructure and active participation of us all.
Regardless of your residential status and international/regional protections, you are responsible for your digital house. It starts from such basic elements like:
- Who is your email account operator?
- Do you use a password manager and two-factor authentication?
- Do you use encrypted messengers to stay in touch with friends and family?
Since these digital building blocks are in daily use, they accumulate a lot of personally identifiable data. It’s vital to choose trustworthy and proven methods/providers. Below I recommend and describe products that can greatly minimize your personal data hoarding and its exploitation.
Google Workspace for an email account
Yes, Google as one of the biggest tech companies is actively engaged in surveillance capitalism. That is obvious for their free services (i.e. Gmail/YouTube accounts) because they monetize it with targeted ads. Google Workspace (formerly G Suite) is their alternative ad-free offering, aimed at businesses but actually, anyone can use it. The key privacy difference is that all Google Workspace accounts are bound with internationally recognized certifications (i.e. ISO/IEC 27018). These certifications are a much better guarantee that Google protects your identifiable information. In comparison, Facebook only operates with an ad-driven model.
My company Nerd on Tour LTD is an official Google Workspace Reseller, and I’d be glad to set up an account for you. It can be on a domain you already have – in my case it’s piotrek@nerdontour.net – or I can find a domain that suits your individual/business needs. Email me or write a message in the form below.
Hey, Fastmail, Protonmail or own web hosting – alternative email providers
Depending on your situation you may prefer choosing a different e-mail provider.
- Hey – is an unconventional webmail service created by Basecamp, that focuses on screening messages before they even reach your inbox. There’re a lot of other practical features developed to optimize your email experience.
- Fastmail – they have been around for many years and their webmail client is similar to other established standards. The main difference is that they’re not part of other major providers like Google, Microsoft, or Verizon (Yahoo, AOL).
- Protonmail – the encrypted email provider was created by professionals working at CERN. They were concerned about the privacy policies of the major (American) email providers and since 2013 Proton is operating under Switzerland regulations. Additionally, they are developing open-source apps and encryption services (i.e. VPN) aimed at people who value online civil liberties.
- Own email hosting – since email infrastructure is based on open standards (POP3, IMAP, SMTP) you can always set up your inbox with the web hosting company or physically on your computer. Mind that there are a lot of details to learn/implement/maintain to have a fully functional and interoperable email account. Spam, spoofing, storage management, SPF authentication are just a few of them to consider.
Lastpass the password manager
Regardless of the security features of your email account, the common practice among people working on the Internet is to use a password manager. Similar to email providers, there’re many password manager solutions depending on how tech-savvy are you. I recommend Lastpass because for many years they’ve been consistently developing practical features while keeping strong encryption and ease of use.
The password manager is a service that stores an encrypted version of all your passwords. It can also generate new unique passwords (highly advisable practice) for every new social media or app that you start to use. The data is secured with your master password, hence the name – Lastpass is the last password that you need to remember to access all other passwords.
Many web browsers (like Chrome, Firefox) and operating systems (macOS, Windows) will often nudge you to save the passwords within their programs. I don’t recommend it because you are locking an important piece of your digital house infrastructure with a provider that doesn’t specialize in securing passwords. In case of web browser or device failure you won’t be able to access the essential “keys”. Keeping passwords in a service like Lastpass will give you the possibility to login from another device/browser and stay in control of your digital keychain.
Authy authenticator for second factor authentication
Passwords like physical keys to your home can be stolen and duplicated, without you noticing it. That’s why every major online service (including social media) encourage users to set up a second-factor authentication (2FA). One time codes (OTC) sent to your mobile phones via SMS, has been consistently proven as an insecure 2FA. It’s fairly easy for a trickster to convince your mobile provider to swap SIM cards or have issues with receiving SMS on spotty signal or while abroad. Therefore it’s best to use a dedicated app for one-time codes.
Authy is the most convenient solution that can store the one-time codes for all important services in your digital house. Mind that if you’re usually using your computer you’re able to add this device to the trusted list and don’t require to put the one-time passwords every time you log in. Yet, if you are using a shared computer at a library or a cyber café, the authenticator is especially important as an additional security layer, beyond your password.
Hushed for SMS codes
Some bank apps or online services won’t yet allow you to set up an authenticator as the second-factor authentication. In that case, I strongly advise using a phone number that is not easily associated with you. You can either buy a cheap prepaid SIM and use it only to receive SMS codes or use an app like Hushed. It’s a mobile app where you can buy a virtual mobile phone number and use it for texting/calling over the Internet. At any moment you can add additional numbers if needed. While the Hushed support page tells you that they don’t officially support receiving automated SMS codes (OTC), in my experience most online services or bank apps work just fine. That includes Google, Amazon, Revolut, Mailchimp, etc.

Encrypted Messengers
There’s currently only one online activity more popular than using social media. That’s messaging. From SMS to WhatsApp and Slack all of these services are primarily focused on writing short texts and sending them directly to a friend or a group. That’s our main method of communication in the digital age and by extension the way to maintain our social relationships. Therefore, the question is – who do you trust to be the “courier”?
There are dozens of messengers and if you want to dive deep into specifics I recommend starting from this Google Sheet maintained by Lance. From my perspective there are two essential components that you should be aware of when using any messenger:
- Is it end-to-end encrypted? Can it be proven by independent research?
- What is the business model behind it?
- How it has been working over the years?
The end-to-end encryption means that the content of the message is not readable for the “courier”. Only you and the receiver can see what has been written because only you two hold digital keys to decrypt it. While many messengers claim to have this kind of encryption (i.e. WhatsApp) only a few have been actually verified by independent researchers (i.e. Element). Why is it important? When you whisper something to a friend’s ear, you expect that it only stays between you two. You should expect similar privacy from the tool you use to “whisper” with a friend over the Internet.
Once you know how secure is their technology, it’s crucial to know their business model. Facebook bought WhatsApp in 2014 and even if they claim end-to-end encryption there’s a whole list of recuring privacy issues around both companies. Most of them are related to an abusive business practice that is the theme of this article. In comparison, Apple has its own iMessage that works only on their devices. Because selling hardware is their primary source of revenue, they don’t monetize the information in the messages.
Signal
If you look for an easy alternative to WhatsApp, that’s used by tens of millions of people I recommend Signal. It’s easy to set up and works like WhatsApp. You just need a telephone number to reach others. The end-to-end encryption has been verified and the non-profit Signal Foundation is striving to keep Signal free and open-source.
Pretty Good Privacy (PGP)
It’s not a messenger per se, but rather an encryption program created in 1991. Since then it evolved and has been implemented in various forms across different services and devices. Thanks to the open-source community you can install and configure it in your code. Or you can use a Chrome/Firefox extension that adds PGP to your Gmail – FlowCrypt. It works with Google Workspace accounts too. Here’s my public key, if you’d like to send me an encrypted email.
Element
Element is a messenger that runs on the Matrix.org protocol. It’s still a niche open-source solution but investment from Automattic and adoption by governments of France and Germany is proving an amazing potential of this platform. Specifically in terms of:
- research-backed end-to-end encryption,
- ability to run it on your own servers,
- interoperability with any other group/user on the network,
- ability to use it on most operating systems and devices,
- using it even when being offline or with a spotty/weak mobile signal.
Also in the context of large teams, companies, and organizations Element can be an incredibly flexible and safe alternative to Slack, Microsoft Teams, or Google Chat. Once you set up your Element (Matrix.org) account – feel free to send me a message.
Web Browsers and browser extensions
Mobile devices are the most popular way of accessing the Internet and fortunately, we can choose our web browsers. They are also our “windows” in the digital house. We can see the world, but depending on which web browser you use and how you use it, the world can see you too.
At this point, it’s vital to understand that digital privacy is a spectrum that needs to be understood in all layers mentioned above – individual, regional, and international. Your security depends greatly on the mix of these layers but also on your:
- profession – i.e. investigative journalist situation is different from a baker,
- social circle – i.e. member of a royal family or leader of work union,
- personal perception and tolerance towards danger.
Therefore I encourage you to read more on how different web browsers work, how can you alter/minimize data hoarding with extensions, and then decide when to use which. Here’s a list of some software that I use:
- Chrome – my Google Workspace account is connected to this browser to make my daily work as a web developer easier. At the same time, my account data is protected – as described above.
- Brave – they offer a suite of practical privacy tools, especially for blocking social media and ad tracking. Therefore I only use it to access my social media accounts and for nothing else.
- Safari – the default web browser on Apple devices has a built-in ad tracking limiter and a Reader Mode that’s especially important when you want to focus on reading an article without distractions.
- Tor Browser – specifically designed to hide your identifiable information behind a global network of circuits maintained by The Onion Router community. It’s crucial to understand what exactly the tor network does and what doesn’t before you start using it full-time.
- HTTPS Everywhere – browser extension developed by Electronic Frontier Foundation to force an encrypted connection with most sites.
- uBlock Origin – very effective open-source browser extension with a public license that blocks ads and ad-related links on websites. The ad lists are maintained by the community.
I wrote more about different methods of staying online while on the go in my Stranded Abroad guide.
Domain Name Server (DNS) alternatives
Your Internet Service Provider (ISP) is usually the first middle-man on a long chain that connects you to the Web. To allow you to connect to different websites they use the Domain Name Server (DNS) that essentially is a long list of all website’s names and their IP numbers. ISPs can track which sites do you visit, how often, and for how long, among other details. Sometimes they use it for commercial purposes (to sell ads or their services) and sometimes it’s the government that wants to monitor citizens.
One of the ways to minimize the collection of such data is by setting a different DNS in your computer, mobile device, or router. Cloudflare is a company known for keeping websites up with its vast Content Delivery Network. They offer a freemium DNS with an IP address 1.1.1.1 that is the fastest DNS resolver with a strong privacy policy. On top of the DNS, you can use WARP and WARP+ services that further secure and optimize your connection speed. They are optional. If you’d like to know more read my previous article about 1.1.1.1 service.

NordVPN the Virtual Private Network (VPN) for encrypted connection
The next step in securing your digital house is by using a Virtual Private Network (VPN). Think of it as a “tunnel” between your digital house and the Internet. It starts in the very beginning, so even the Internet Service Provider can no longer record details about your online activity. Because the tunnel can be set for a specific region (i.e. UK or Singapore servers), you can also access geo-restricted content from anywhere. One of the leading VPN providers is NordVPN and I recommend using their services.
Convenient apps for all major operating systems and browser extensions allow you to connect up to six devices at the same time. They offer over 5500 servers in dozens of countries, which means that you can get high speeds regardless of your location. Additionally, they implemented a next-generation protocol called WireGuard, which is faster and more reliable than current VPN protocols.
It’s important to mention that “free VPN” services offered in some web browsers or apps can be even worse in terms of data hoarding. Because literally all your Internet traffic is routed via VPN servers of another company I strongly encourage you to use only paid VPN providers that have a good track record and strong privacy policy.
Apple devices – the best ratio between convenience/privacy/speed
All of the solutions described above are software-based. It means that you can use them right away on the devices that you already have. Yet, you can streamline the process of building your digital house by choosing the right hardware. Mind that I’ve been tinkering with my desktop computers and mobile devices since I was a kid. For years I was convinced that assembling my computer and running Windows is the only right path. The same was true for me when Nokia was dominating the cell phone industry. Both of these things changed when I started to work as a tour leader and web developer.
In short, Apple products have been consistently reliable since I’ve started using them in 2011. That’s especially crucial when I was in:
- a place with spotty/weak mobile/Wi-Fi network,
- transit for 20+ hours without a way to charge my devices,
- need to quickly check the Internet, call someone, or edit and send an important file.
With Apple accessories, phones, tablets, laptops I never had any major problems that would affect my workflow. No firmware update, broken app, or malicious file ever negatively affected my devices. Therefore, with Apple, I can focus on what is important to me. Whether I want to work, play, or chill.
Moreover, in recent years we can observe that Apple is pushing practical privacy features that truly break the abusive data business practices. At the same time, Microsoft is going in the opposite direction. An example of that is by recording all user activities on a new Windows computer by nudging for Express Settings setup. The same is true when you compare the iPhone with Android phones.
Everything around you that you call life was made up by people that were no smarter than you. And you can change it, you can influence it… Once you learn that, you’ll never be the same again.
Steve Jobs co-founder of Apple

How to Build Better Systems?
We are living in truly fascinating times, where the rate of change is faster than anything before. The Internet has been the backbone of all technologies and social phenomenons that are now dominating the globe. As it’s the case for many emerging industries and uncharted territories, there’s a turbulent period. That’s when few dominating businesses are profiting from the status quo, while the undermined public is seeking better and equal solutions.
Yes, this kind of conflict can turn into violence and erosion of democracy across the board. Yet I’m a big believer in conscious and ongoing discourse. The freedom of thought, way of life, and enormous economic growth that happened in the last few hundred years wouldn’t be possible without Enlightenment thinkers, social activists of the 19th/20th century, and eradication of illiteracy. The current digital age creates a whole set of problems that require us to build appropriately fit systems.
These better systems have to be:
- more just,
- unlock equal opportunities,
- representing the diverse culture of all participants.
While I don’t have exact solutions for all the issues that surfaced in this article, I do pay attention to many projects and people who are on a right track. In many instances, it’s a work in progress but you can contribute regardless of your location and tech literacy.
The solution is not less tech. It’s better tech.quote from an interview with Kevin Kelly founding executive editor of Wired magazine, book author, technologist
I consider myself a humanist and technologist
Computers have been my source of frustration. Every day when I wanted to play video games or browse the Internet, things would break. I thought I didn’t have enough patience for this vicious circle of a break, fix, repeat. At the same time, I discovered the beauty of the written word and the vast world of philosophy. They also required time and focus, that I thought I didn’t have.
Over the decades I realized the significance of humanistic domains such as ethics, concepts of freedom, and reasoning. Later came meditation, yoga, self-awareness, and mindfulness that further strengthen the humane values. With them, I’ve gained the perspective to treat technology as useful tools, not as a center of my life.
Computers, phones, and Internet services (including social media) will stop working. That’s their inherited nature. We’ll replace them with new devices and Internet solutions, better adjusted to our future needs. Still, we’ll remain humans. With all our strong emotions, ever-expanding thoughts, and one crucial super-power that differentiates us from all other knowns species. Collaboration.
The following examples are showing how better systems can be built, through our conscious collaborative efforts.
Participatory democracy and publicly available Facebook ads manager
Taiwan mentioned twice already in this article is an inspiring example, where grass-root open-source social movements started in 2012 resulted in appointing one of the hacktivists, Audrey Tang as the first Digital Minister. She’s also a transgender person and that further shows how progressive is the democratic system of this country. But Taiwan is not the only place that embraces participatory democracy on a nation-wide scale.
Estonia is another great case of a nation that already in the ’90 decided to build a proper digital infrastructure for all citizens. Now they’re the pioneers in protecting citizens’ personal data while enabling online voting and convenient access to all governmental institutions. Their forward-thinking international programs, like e-residency, company incorporation, and digital nomad visa are proving the efficiency of their better systems on a global scale.
While active participation in democratic institutions is vital in building resilient social structures it also needs to keep in check corporations. Particularly when their products significantly affect democratic processes – like Facebook ads that anybody can buy and target specific voters. As always Facebook Inc. claims to do “everything” to be more transparent, yet only when they are sufficiently pressured by a government, the corporation gives proper access to their data. This is how Taiwanese citizens, journalists, activists, and government officials can monitor who exactly is sponsoring an influential ad. Every country should have full access to Facebook Ads Library by default and I wish to see it happen in the near future.
If you’re not paying for it, you’re the product.Quote attributed to many people, depending on the time period
Be a conscious Internet Creator
Since the very beginning of the Internet, the idea of making it free and publicly available dominates throughout decades. I acknowledge that the “public park” characteristic of the Web allowed legions of people like me to join, learn, and grow immensely. If you are curious, the concept of “free Internet” is deeply conceptualized in the following sources:
While social media further extend the “free” service on the Internet, there’s one highly significant factor, that differs from previous mediums. Their algorithms are optimized for the newest and most attention-grabbing content. It’s the race to the bottom, where currently TikTok is leading the way by artificially enhancing “popularity metrics” – impressions, views, likes, etc.
In contrast, timeless songs, books, blog posts, and podcasts are being found, recommended, and absorbed over and over again. Please mind, that due to technological convergence new media are being invented and there’s no fine line between the type and likelihood of it being re-discovered. Nevertheless, you are – as the creator – in control of your creative life cycle.
There’s a fundamental difference between publishing a heartfelt post on your blog and putting it as a story on Instagram. The first will live for years, allowing you and your readers to reflect on the past moment in time. The second is immediately filtered via algorithms to measure its attention potential and lives for twenty-four hours until it’s locked from the public and stored on corporation owned servers.
As the Internet creator myself, I’m always choosing long-lasting creations – like blog posts and podcasts. For me social media can be a useful tool to further promote and reach other like-minded folks. But it’s never a core of my Internet presence. The creators I follow for years are also consistently building their massive back catalog while their approach to social media varies greatly.

Inspiring Internet Creators
- Vlogbrothers – Hank and John Green that started vlogging back in 2007 often talk about understanding Internet platforms as our new “physical” social spaces. Hank also published two great sci-fi novels that perfectly encapsulate what can happen if the virtual world of social media completely takes over our lives (An Absolutely Remarkable Thing and A Beautifully Foolish Endeavor).
- Tim Millgram – video producer who specializes in recording beautiful choreographies. In many cases, his videos are more popular than the official music clips for a given song (i.e. Water Dance). Focus on showing moves by the great dancers has the same high value at the time of the publication as it is today.
- Stratechery – deep analysis of the tech from a Ben Thompson who has worked at Apple, Microsoft, and Automattic before shifting to full-time blogging. I also enjoy his conversational Exponent podcast run together with James Allworth (head of Innovation at Cloudflare).
- Signal vs Noise – David Heinemeier Hansson and Jason Fried are very vocal technologists showcasing the importance of remote work, sustainable business growth, and a humane work environment in the tech industry. Besides the blog, I recommend reading their non-conformist books.
- Tim Ferris Show – long-form conversations with experts in different fields of life is the most intriguing reason, why I’m consistently listening to this podcast. Often times the valuable bit is hidden deep within honest interaction between the guests and the host. If you want to train your listening skills and attention span I deeply recommend Tim Ferris Show.
- Dan Carlin’s Hardcore History – this show feels like a very well narrated history audiobook with a new episode every few months. Detailed cultural perspective helps better understand the motivations of past rulers and decisions that shaped civilizations.
The above examples of consistent Internet creators are also showing a wide spectrum of mediums that you can choose, as a creator. Those who have been through a couple of technological adoption cycles, correctly recognize that finding your own strengths is extremely important. Self-awareness tells you which kind of storytelling fits you more. The general types are:
- Written word,
- Voice/sound,
- Visuals.
Therefore, while technological advancements are constantly blending these three, knowing your type, will help you excel. Especially, when the dominant technology or platform will change.

Contribute to the Internet culture
Much like traditional culture, every repeated behavior on the Internet is building its culture. Currently, when social media are dominant, it’s vital to understand that their power comes from every little action, everyone makes. Your contribution can be as little as a like on friends picture to as much as managing an influential group/profile on one of the platforms. Your conscious decisions affect the vibe and influence of social media at large.
That’s one of the reasons why I’m focusing on building long-lasting content on my own hosting – this blog, podcast, my customers’ websites, etc. The creative work I put in today is useful and relevant for years. I’m also in control of these assets. All written words, graphics, themes, and code are stored on servers and regularly backed up with cloud services.
Keep in mind that the Internet offers a huge variety of tech solutions, and you can be a valuable contributor, by mindfully choosing established platforms with high positive impact. You don’t have to build things from scratch. Here are some of them:
- Wikipedia – completely unique idea of a free and editable encyclopedia that conceptually didn’t make sense. Time has already proven the immense value of establishing a universal knowledge base and striving for the most objective perspective. Contribute by improving topics you know best and over time you can create your own articles.
- Stack Overflow – as the name suggests the support site was created primarily for coders but over time they expanded to non-strictly technical fields. Anyone can ask and answer a question and if it resonates with other people it’ll be upvoted. You don’t have to be a developer to join the community and share your knowledge.
- Nerdfighteria – a positive bunch of people that started gathering around vlogbrothers YouTube channel and now exist in multiple Internet spaces. If you enjoy the humor, melancholy, ingenuity, and charity efforts of Hank and John Green – come and join nerds that fight to decrease world suck.
- Kurzgesagt – high-quality scientifically rigorous and educational videos are attracting science-oriented folks. If you, like me, enjoy how this Munich-based company is telling stories – you may find valuable connections with fellow fans of the show.
- Nomad List – my go-to community of digital nomads created around Pieter Levels’ website. Regardless if you just starting or you are a seasoned nomad, this is the Internet space to be. You can suggest data sources or improvements, share/upvote topics on the forum, or meetup virtually or IRL with people in the same location.
Work with great minds and with strong ethics
While contributing your free time to expand human knowledge and togetherness can be satisfactory, you may also want to make it into a career. More and more companies are hiring ethics advisors, social activists, and humanists of all kinds. Both governments and private sectors are recognizing the importance of humane values. They need to be engraved and constantly verified, so there’s a market demand for ethical specialists.
Mind that established big tech corporations, including Facebook, has been claiming their moral values since the dawn of Silicon Valley. Similarly to oil companies, we need to watch their repeated actions, not PR communications. Of course, if you are up for challenges, you may try to join them and try to really improve their system from inside.
Additionally, there are technologies that have bigger disruptive potential than social media – like artificial intelligence. You may want to explore job opportunities in DeepMind or OpenAI, that seems to focus a lot on the ethical implications of their research. Besides that, you also have non-governmental organizations like the Center for Humane Technology or Institute for the Future. They create ethical guidelines, produce impactful content, and put pressure on corporations and governments.
Create a new Internet product
There is one particular group of people on the Internet that inspire me every single day. We call them makers and they create their own original Internet-based products and services. Often times by learning how to code from scratch or leveraging their niche expertise. They represent the unconstrained creative force on the Internet. In many cases, their monetary success is remarkable proof that anyone, anywhere can make money online on their own terms.
Indie Hackers
My favorite place to learn and mingle with fellow makers is called Indie Hackers. Started as a community-focused website by Allen Courtland and was acquired by finance platform Stripe in 2017. Projects are divided into categories and makers are sharing their ups and downs, including the income figures. Ingenuity and endurance are the two most visible qualities among members of the Indie Hackers community.
Product Hunt
The Internet-based projects are often called products – regardless of their form and function. With Product Hunt – another community-driven website – makers can popularize their fresh creations. Members are primarily revolving around tech themes, but every so often non-tech products can become the most upvoted listing of the day, week, or month. Many makers are using Indie Hackers and Product Hunt in tandem to tell their journey and reach out to like-minded folks.

MAKE book
The aforementioned Pieter Levels has an impressive track record of being voted for Maker of the Year on Product Hunt twice and reaching the top income charts on Indie Hackers. His “Make” book is in my opinion the best blueprint to start profitable projects on the Internet. In Pieter’s typical fashion, the book itself challenges the norms. It’s self-published as a web page and after introduction, the words are scrambled with an original encryption method. Once you buy it, the content is unlocked, and you can read it directly within the web browser.
List of Internet products created by fellow makers
- No Code API – many online services offer APIs to easily exchange information with external servers. Fellow maker Mohd Danish created a convenient way for people who would like to connect these services without coding.
- The Mac Index – as a nomad who usually buys Apple products in different countries I like to know which regions have the best deals. Wafiq word played with “the Big Mac Index” and is listing iPhones, Macs, Airpods, and all other Apples based on their official price and current currency rates.
- Simple Ops – if you run any website you should be aware of downtime and performance standards that affect your search engine optimization and user experience. Hakr created a tool to keep track and improve your site.
- Traf iOS icons – a fascinating example of a designer, who understood the unique opportunity of the icon customizing feature released in iOS 14. Traf made over 100 000 USD in six days from a one-time purchase set of graphics that stylize an iPhone menu screen.
- Open Peeps – cartoonish human characters have been always a convenient way to tell a story – i.e. for educational or commercial purposes. Pablo Stanley created a “pay what you want” library of such figures with exchangeable body features. It’s like Lego for visual content designers.
- Remote OK – most popular job board for people looking for remote work. Very minimalistic and efficient. That’s another project by Pieter Levels.
- Banner Bear – a very efficient tool to automatically generate visual content for social media and eCommerce purposes. Jon Yongfook after experimenting with lots of other projects discovered that Banner Bear has the biggest potential.
Think like a parent – how to establish effective safety guidelines?
Absolute creative freedom is an important value that enables rapid and fruitful growth of the whole Internet. Yet, we can never forget, that what we do and how we do things on the Internet always affect people of all ages. We:
- build habits around phones and screens,
- spend attention and time on online services,
- earn and manage our money with digital tools.
Repeated actions create cultural norms in which kids are growing up. Even if you don’t have or plan to have children, the parental perspective is very practical. It allows you to use compassion and understand what kind of dangers the vulnerable people are exposed to.
Oversharing of privately identifiable data is one of the cultural norms. Carissa Véliz, the AI ethics professor at Oxford University is challenging this notion, by emphasizing that – Privacy is Power. That’s also the title of her book in which she’s suggesting establishing new social and cultural norms of online privacy. Following this example, if our new norms can protect a common person it can also extend to those more vulnerable.
Jonathan Haidt interviewed in Social Dilemma was describing the correlation between suicidal hospital admissions of Gen Z and their use of social media on mobile devices. He further explores the topic in the Undivided Attention podcast, pointing to other social issues we solved in the past. For example, alcohol is one of the products that we restrict legally and socially, allowing it only for adults.
Another critical argument has been made by Christopher Wylie – a whistleblower that exposed the Cambridge Analytica scandal. He describes civil engineers and architects as a specialist that are bound by oaths and quality standards. Because bridges or buildings are used by the masses and are fundamental for everyday infrastructure, they cannot be faulty. A common person and especially a child, don’t have to know what makes a construction safe to use. Engineering standards have been developed for the safety of us all. Wylie suggests that software engineers should also be obliged by a similar set of regulations.
Lastly, there’s the “social media CEO” trap. The cheerful comedy series “Good Place” that takes place in the afterlife, made a joke that this kind of CEO is the last step before a demon reaches its final form. It’s an obvious reference to the fact that many big tech executives don’t allow their own kids to use social media. This highly hypocritical position has been also shown in Social Dilemma, where many interviewees honestly admitted the social media ban in their families.

Additional resources related to Social Dilemma
Here are links to materials that can help you deepen knowledge and allow for thoughtful collaboration to build better systems:
ShockOne’s Follow Me song is a great summary of this article
Build Better Systems – Closing Thoughts
I don’t pretend to have all the answers. Nevertheless, I’m ready to ask difficult questions. Since I remember, questions have been my favorite though experiments. They “happened” to me long before machines and the Internet became a dominant force. Every human generation has its set of problems to solve. It appears that data privacy in the digital age is the centerpiece of our issues.
Keep in mind that like climate change, it requires effective collaboration on the individual, regional, and international level. We need to tap into collective wisdom which may or may not mean listening to the most charismatic person in “the room”. Conversely, when the social norm is causing problems, be the one to apply better alternatives for the benefit of us all.
Mindful self-awareness will reveal your strengths. Double down on them, because you never know how positively impactful your creation can be. At the same time default to kindness. Compassion can lead you very far. Especially since the current state of affairs doesn’t have villains. It’s a result of many independent phenomenons that merged and are being abused.
Lastly, remember that you build your own system every day. It’s your digital habits, social relationships, and online decisions that form patterns. Every little thing that you do or more importantly, don’t do, creates the system. We get this far by the ability to work together. We can go further if we continue to collaborate.






Discussion